FREE K-12 AI LITERACY COURSES FOR THE 2025-2026 SCHOOL YEAR! Learn more here.
- Skill Struck
- Course Catalog
- AP Computer Science Principles
AP Computer Science Principles
An in-depth course to understand a variety of computer science topics and programming principles at a college-level instruction. This course is endorsed by the College Board.
1 year Course
Voyage
AP Curriculum
Year
Python
9th grade
10th grade
11th grade
12th grade
- Course Summary
- Course Outline
- Standard Alignment
- Course Project
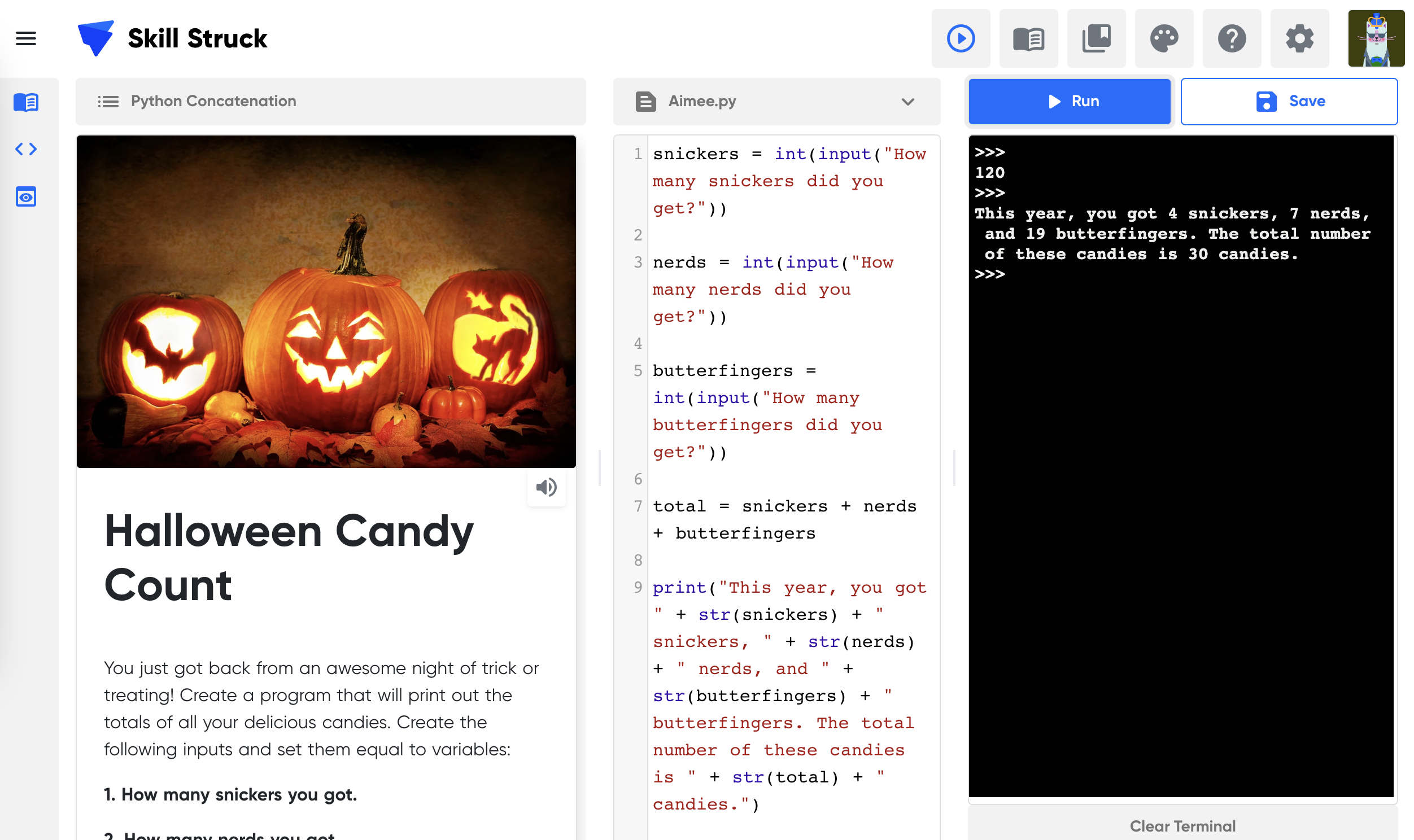
AP Computer Science Principles is an introductory college-level computing course that introduces students to the breadth of the field of computer science. Students learn to design and evaluate solutions and apply computer science to solve problems through the development of algorithms and programs. They incorporate abstraction into programs and use data to discover new knowledge. Students also explain how computing innovations and computing systems—including the internet—work, explore their potential impacts, and contribute to a computing culture that is collaborative and ethical. *This course is endorsed by the College Board.
-
Unit 1: AP CSP.1 Welcome to the AP Class!
Learning Outcomes:
Students are oriented to the AP Course and explore what is in store for them.
Topics covered:
Orient to the Platform
Standard alignment:
2-AP-11, 2-DA-07
-
Unit 1: AP CSP.4 Accessibility & HTML Basics & Headings
Learning Outcomes:
Students will explore different ways to take a computational artifact and make it more accessible for more kinds of people. They will learn how to add HTML headings.
Topics covered:
Accessible Interventions Activity
Headings
Standard alignment:
2-CS-01, 2-CS-02, 2-NI-06, 2-DA-07, 2-AP-11, 2-AP-16, 2-IC-20, 2-IC-21
-
Unit 1: AP CSP.9 Computers and Your World & Background Color/HTML Title
Learning Outcomes:
Students will add more dynamic functionality to their websites as tehy learn how to add background color and a title to their websites.
Topics covered:
Background color
HTML title
Standard alignment:
2-IC-21, 2-AP-11, 2-AP-16, 2-DA-07
-
Unit 1: AP CSP.13 App Design & Text Align
Learning Outcomes:
Students learn how to add text align in HTML. They design an app and map out all the hardware and software that would be needed to make their app a reality.
Topics covered:
Text Align
App Design
Standard alignment:
2-AP-11, 2-AP-16, 2-DA-07, 2-CS-02
-
Unit 1: AP CSP.14 Advertisement Analysis & Links
Learning Outcomes:
Students will analyze different advertisments and asses how well they reach their target audiences. They learn how to add links to their websites.
Topics covered:
Advertisement Analysis
links
Standard alignment:
2-DA-07, 2-DA-08, 2-AP-11, 2-IC-20, 2-IC-22
-
Unit 1: AP CSP.17 Digital Footprint & Background Image
Learning Outcomes:
Students learn what a digital footprint is and explore how permanent information on the internet really is. They learn to add background images to their HTML file.
Topics covered:
History of Computers
Background Images
Standard alignment:
2-IC-20, 3A-IC-24, 3B-IC-25, 3B-IC-26, 3A-AP-13, 3A-AP-16, 3A-AP-17, 3A-AP-18, 3B-AP-14, 3B-AP-19, 3B-AP-21, 3B-AP-22
-
Unit 1: AP CSP.19 Image Links & Marquees
Learning Outcomes:
Students will increase engagement on their websites by learning how to add image links and marquees.
Topics covered:
Image Links
Marquees
Standard alignment:
2-DA-07, 2-AP-11, 2-AP-13, 2-AP-16, 2-AP-17
-
Unit 2: AP CSP.3 Algorithms in Computer Programming & Events
Learning Outcomes:
Students practice adding events to their algorithms as they navigate through the puzzle. These events manipulate the environment of the puzzle.
Topics covered:
Algorithm Puzzle
Sequencing
Events
Standard alignment:
-
Unit 3: AP CSP.6 Legal and Ethical Concerns in Innovations & Converting
Learning Outcomes:
Students will explore different political and ethical issues that come up alongside different computer innovations. They will discuss the presence of bias in innovations.
Topics covered:
Social and Political Impacts of Innovations
Bias
Standard alignment:
3A-IC-24, 3A-IC-25, 3A-IC-30, 3B-IC-25, 3B-IC-26, 3B-IC-27, 3B-IC-28, IOC-1.D.1, IOC-1.D.2, IOC-1.D.3, IOC-1.F.9, IOC-1.F.8, IOC-1.F.11
-
Unit 3: AP CSP.12 Party Planner
Learning Outcomes:
Students practice breaking down a big project (planning a party) into smaller, more manageable tasks.
Topics covered:
Break Down Big Probems
Standard alignment:
3A-AP-13, 3A-AP-16, 3A-AP-17, 3A-AP-18, 3B-AP-10, 3B-AP-11, 3B-AP-14, 3B-AP-21, 3B-AP-22, 2-AP-11, 2-AP-17, 3A-NI-05, 3A-AP-15
-
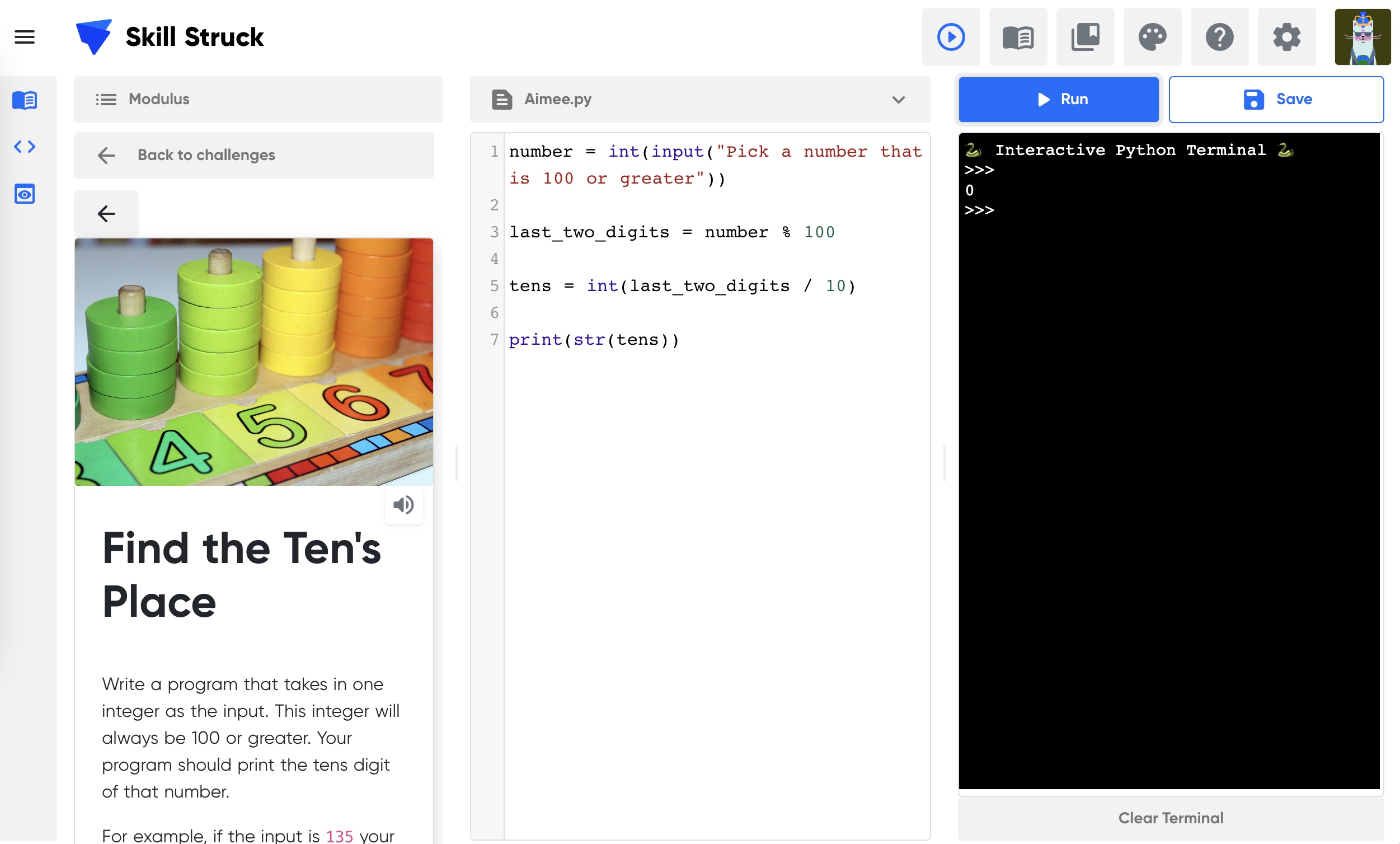
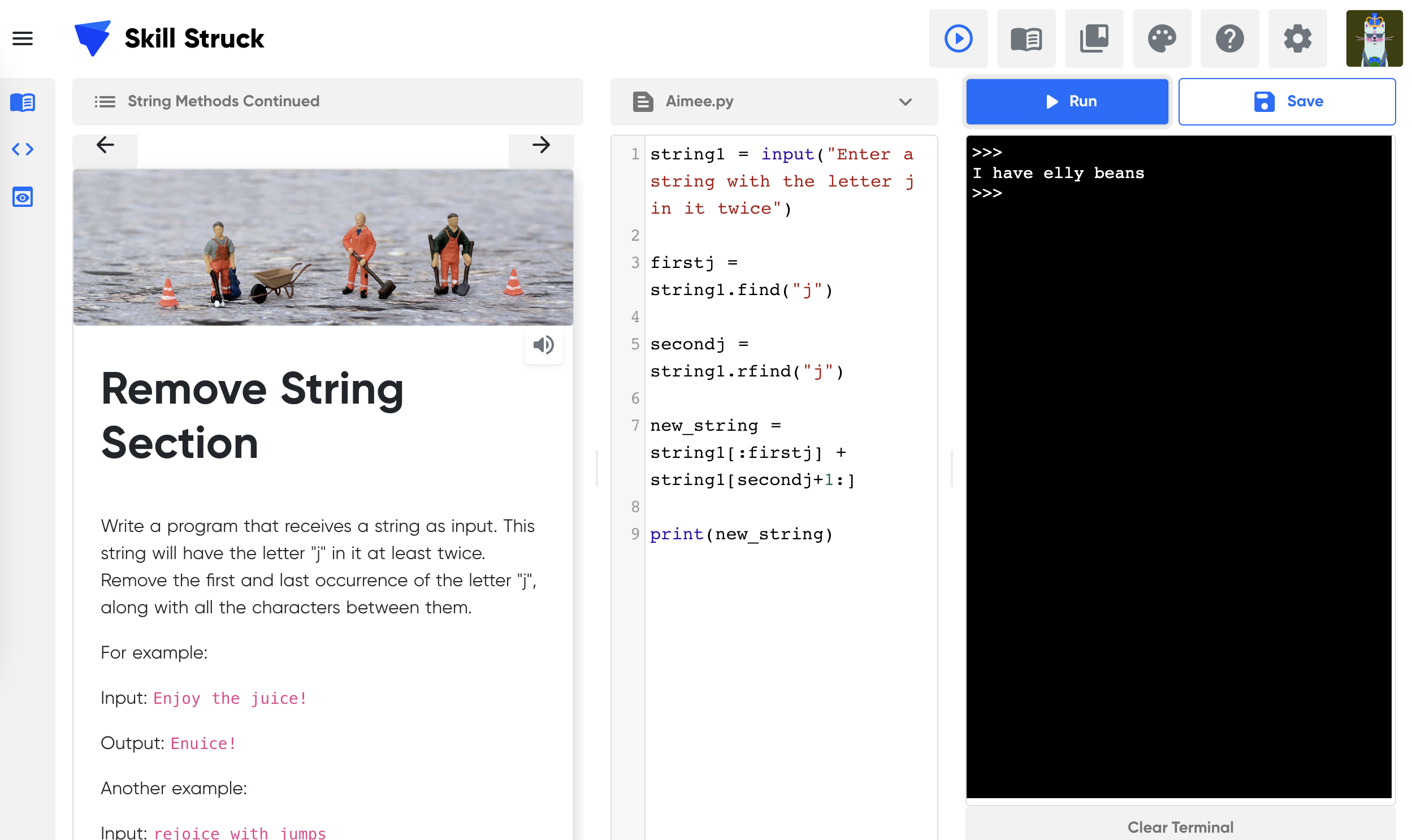
Unit 4: AP CSP.1 Computer Boundaries & String Methods Continued
Learning Outcomes:
Students examine how technology affects their mental health and discuss possible boundaries they might want to implement in their lives. They learn more about Python strings.
Topics covered:
Strings
Computer Boundaries
Standard alignment:
2-AP-17, 2-AP-11, 3A-IC-24, 3B-IC-26, 3B-AP-22, 3B-AP-21, 3B-AP-19, 3B-AP-14, 3B-AP-11, 3B-AP-10, 3A-AP-18, 3A-AP-17, 3A-AP-16, 3A-AP-13
-
Unit 4: AP CSP.10 Troubleshooting Scenarios & If Statements
Learning Outcomes:
Students practice troubleshooting techniques in different posed scenarios. They learn to add if statements to their Python code.
Topics covered:
If Statements
Troubleshooting
Standard alignment:
3B-AP-12, 3A-AP-13, 3A-AP-16, 3A-AP-17, 3A-AP-18, 3B-AP-10, 3B-AP-11, 3B-AP-14, 3B-AP-19, 3B-AP-21, 3B-AP-22, 3A-CS-03, 2-CS-03, 2-AP-11, 2-AP-13, 2-AP-17, 3A-AP-15
-
Unit 4: AP CSP.12 Debugging Strategies
Learning Outcomes:
Students examine how to use troubleshooting techniques to find bugs in their code.
Topics covered:
Debugging Strategies
Troubleshooting
Standard alignment:
3B-AP-22, 3B-AP-21, 3B-AP-19, 3B-AP-14, 3B-AP-12, 3B-AP-11, 3B-AP-10, 3A-AP-18, 3A-AP-17, 3A-AP-16, 3A-AP-15, 3A-AP-13, 2-AP-17, 2-AP-14, 2-AP-13, 2-AP-12, 2-AP-11, 2-DA-07, 2-CS-03
-
Unit 4: AP CSP.20 Team Project Continued
Learning Outcomes:
Students will do an activity to better get to know their team and discover new ways to understand how teammates work. They will have time to work on their team project.
Topics covered:
Get to Know Your Team Activity
Team Project Time
Standard alignment:
2-AP-11, 2-AP-13, 2-AP-15, 2-AP-17, 2-AP-18, 3A-AP-13, 3A-AP-16, 3A-AP-17 , 3A-AP-18 , 3B-AP-10 , 3B-AP-11, 3B-AP-14, 3B-AP-19, 3B-AP-21, 3B-AP-22, 3A-AP-22, 3A-IC-27 , 3B-AP-17, 3B-AP-20 , 3B-AP-23 , 3B-AP-23 , 3A-AP-19
-
Unit 5: AP CSP.10 Binary Art Project
Learning Outcomes:
Students learn how binary notation is converted into letters and text as they explore how anything can be represented as long as they have a key. Students examine the need for Unicode to replace the ASCII table in order to include people from all backgrounds.
Topics covered:
Using a Key to Represent Anything with Binary
ASCII Table
Unicode
Standard alignment:
3A-CS-01, 3A-DA-09, DAT-1.A.2, DAT-1.A.6, DAT-1.A.7
-
Unit 6: AP CSP.1 Computer Science Advertisement & Animal Tracking Introduction and Variables
Learning Outcomes:
Students learn how to represent information using variables as a placeholder. This level of abstraction preps the students to track data on the elephant seal.
Topics covered:
Variables
Standard alignment:
MS-ESS3-4 Earth and Human Activity, MS-ESS3-5 Earth and Human Activity, MS-LS2-1 Ecosystems: Interactions, Energy, and Dynamics, MS-LS2-2 Ecosystems: Interactions, Energy, and Dynamics, MS-LS2-3 Ecosystems: Interactions, Energy, and Dynamics, MS-LS2-4 Ecosystems: Interactions, Energy, and Dynamics, , 2-DA-07, 2-AP-11, 3A-CS-01, 3B-AP-11, 3B-DA-05, 3B-DA-06, 3B-DA-07
-
Unit 6: AP CSP.4 Animal Research Continued & Animal Tracking and If Statements and Conditionals
Learning Outcomes:
Students increase their code's ability further as they learn to add if statements to specialize what their inputs are doing. This allows them to create hypotheses about the elephant seal's movements through the Pacific ocean.
Topics covered:
If Statements
Standard alignment:
MS-ESS3-2 Earth and Human Activity, MS-ESS3-3 Earth and Human Activity, MS-ESS3-4 Earth and Human Activity, MS-LS2-1 Ecosystems: Interactions, Energy, and Dynamics, MS-LS2-2 Ecosystems: Interactions, Energy, and Dynamics, MS-LS2-3 Ecosystems: Interactions, Energy, and Dynamics, MS-LS2-4 Ecosystems: Interactions, Energy, and Dynamics, , 2-DA-07, 2-AP-11, 3A-CS-01, 3A-AP-13, 3B-DA-05, 3B-DA-06, 3B-AP-11, 3B-DA-05, 3B-DA-06, 3B-DA-07
-
Unit 6: AP CSP.5 Human Impacts & Animal Tracking Engineering Project
Learning Outcomes:
Students combine all of what they've learned in this unit into an engineering project. They create a program for a device that would keep track of the animal's movements from day to day and generate a log of data. This data can be used for further conservation efforts.
Topics covered:
Variables
If Statements
Conditionals
Converting Data Types
Inputs/Outputs
Standard alignment:
MS-ETS1-1 Engineering Design, MS-ETS1-2 Engineering Design, MS-ETS1-3 Engineering Design, MS-ETS1-4 Engineering Design, 2-DA-07, 2-AP-11, 3A-CS-01, 3A-AP-13, 2-AP-13, 3B-DA-05, 3B-DA-06, 3B-AP-11, 3A-AP-14, 3A-IC-26, 3B-DA-05, 3B-DA-06, 3B-DA-07, 3B-AP-15
-
Unit 6: AP CSP.8 Scatter Plots & Correlation/Causation
Learning Outcomes:
Students will conduct their own research through sending out a google form to their classmates. They will discuss data privacy and explore how they feel about their personal data.
Topics covered:
Market Research Activity
Data Privacy Discussion
Standard alignment:
2-CS-01, 2-DA-08, 2-AP-15, 2-IC-20, 2-IC-22, 2-IC-23
-
Unit 7: AP CSP.3 Complex Problems & Adding to Lists in Python
Learning Outcomes:
Students explore different problems that computer programs have a difficult time analyzing. They will discover different heuristics for narrowing down acceptable answers. They will discuss difficult problems such as the halting problem and traveling salesman challenges.
Topics covered:
The Traveling Salesman
Undecidable Problems
Standard alignment:
AAP-4.A.2, AAP-4.A.8, AAP-4.A.9, AAP-4.B.1, AAP-4.B.2, AAP-4.B.3
-
Unit 7: AP CSP.4 Magic Carpet & Logical Thinking
Learning Outcomes:
Students will discover their natural tendencies towards problem solving through a Magic Carpet activity. They will practice logical thinking techniques.
Topics covered:
Logical Thinking
Magic Carpet
Standard alignment:
2-AP-11, 2-AP-13, 2-AP-14, 2-AP-15, 2-AP-17
-
Unit 7: AP CSP.8 Arctic Excursion
Learning Outcomes:
Students will embark on an arctic excursion and discover ways to break down big projects into smaller chunks in order to achieve a task.
Topics covered:
Fan Test
Arctic Excursion Processing
Actic Excursion
Standard alignment:
2-AP-13, 2-AP-15, 2-AP-17, 2-AP-18
-
Unit 7: AP CSP.9 Metadata & If Statement in a For Loop
Learning Outcomes:
Students explore the different kinds of metadata and discover what each is commonly used for. They identify the different between data and metadata.
Topics covered:
Structural Metadata
Administrative Metadata
Descriptive Metadata
Standard alignment:
3A-DA-10, DAT-2.B.1, DAT-2.B.2, DAT-2.B.3, DAT-2.B.4, DAT-2.B.5
-
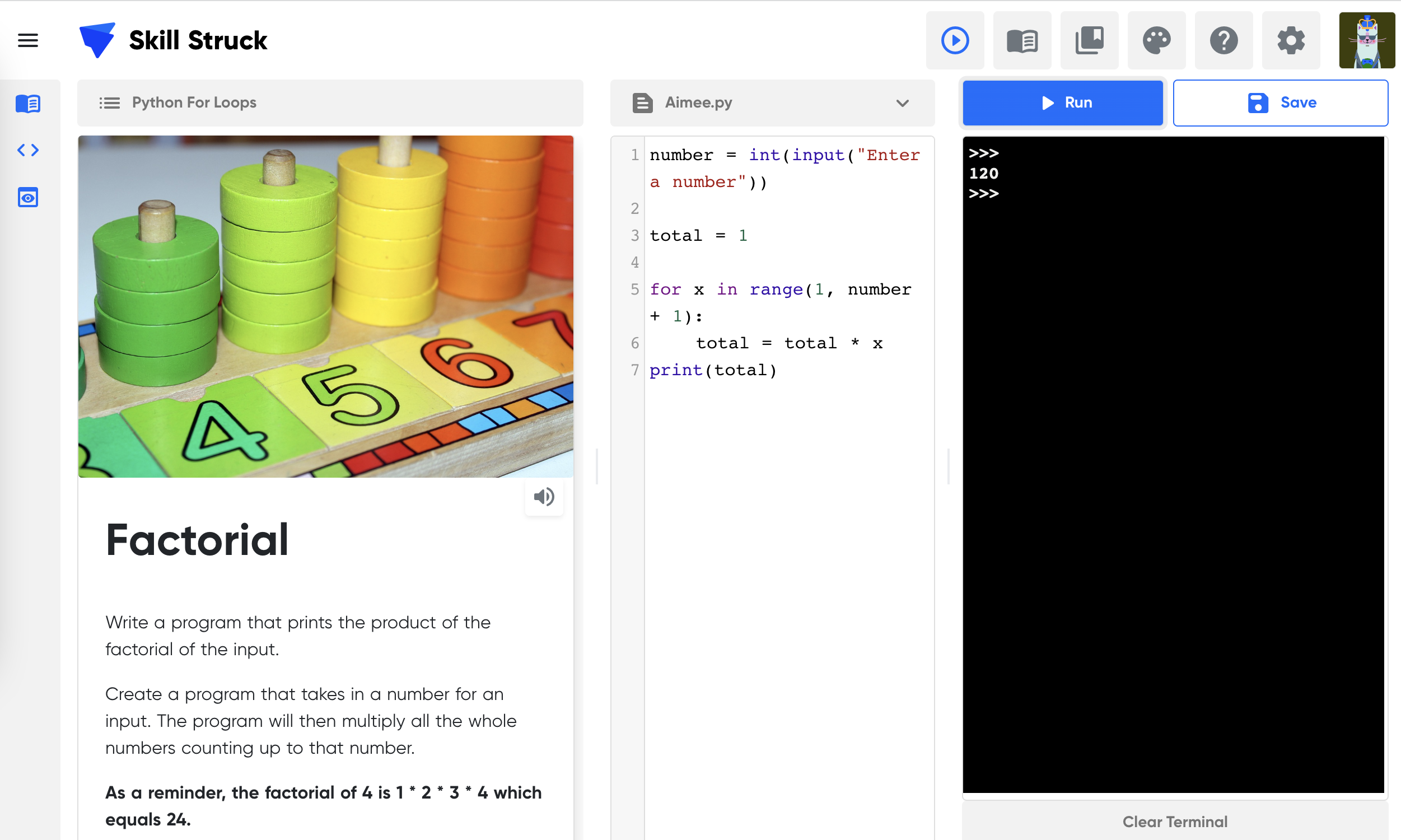
Unit 7: AP CSP.10 Secret Shapes & Add the Factorial
Learning Outcomes:
Students further explore their team problem solving strategies in an unplugged activity where they work together to create shapes from string. They will work on a factorial Python project..
Topics covered:
Problem Solving
Error Handling
Standard alignment:
3B-AP-21
-
Unit 7: AP CSP.14 Teachable Machine
Learning Outcomes:
Students will practice creating a machine learning program.
Topics covered:
Machine Learning
Standard alignment:
3A-AP-13, 3A-AP-16, 3A-AP-17, 3A-AP-18, 3B-AP-10, 3B-AP-11, 3B-AP-14, 3B-AP-19, 3B-AP-21, 3B-AP-22, 2-AP-11, 2-AP-13, 2-IC-20, 2-AP-17
-
Unit 7: AP CSP.18 Simulation
Learning Outcomes:
Students play around with random and how it can help generate simulations. They discuss when a simulation might help save resources. They will analyze the pros and cons of a simulated environment.
Topics covered:
Simulation
Build a Simulation
Bias in Simulations
Standard alignment:
3A-AP-17, 3B-DA-07, AAP-3.F.1, AAP-3.F.2, AAP-3.F.3, AAP-3.F.4, AAP-3.F.5, AAP-3.F.6, AAP-3.F.7, AAP-3.F.8
-
Unit 8: AP CSP.2 Python Review
Learning Outcomes:
Students will review key Python concepts
Topics covered:
Review
Standard alignment:
-
Unit 8: AP CSP.4 Python Review
Learning Outcomes:
Students will review key Python concepts
Topics covered:
Review
Standard alignment:
-
Unit 8: AP CSP.5 Computers and Your World Review
Learning Outcomes:
Students will review computers and your world concepts.
Topics covered:
Review
Standard alignment:
-
Unit 8: AP CSP.6 How Computers Represent Information Review
Learning Outcomes:
Students will review how computers represent information and binary.
Topics covered:
Review
Standard alignment:
-
Unit 8: AP CSP.7 The Internet Review
Learning Outcomes:
Students will review how the internet works.
Topics covered:
Review
Standard alignment:
Download the 2022 Skill Struck Standards Alignment + Correlation Guide to view a general list of our standard alignments, or find your state's specific alignment below:
AP Computer Science Principles
In this course, students will complete challenges that help solidify concepts as they use skills in a variety of ways. In order to complete tasks, students will creatively apply what they've learned by using different approaches to reach a goal. This experience closely follows challenges they would face in a technical interview, allowing them to practice.
180 Student Activities
128 Teacher Resources
32 Checkpoints
3 Pre/Post Test
-
674 Quiz Questions
Autograder
English and Spanish
Skill Struck Reviews

Having a mapped out, structured way to learn and experience the Computer Science curriculum really freed up time for me to give students one-on-one attention. It also gave me more opportunities to give the students additional programming assignments to help them understand the concepts better.
Scott Couch
CS Teacher, Maeser Prep Academy

The program and the people behind it are innovative, intelligent, and organized. The platform is very user-friendly and l have been able to guide my students easily through the curriculum.
Dillon Gilpin
High School CS Teacher, Duchesne County School District

All of the content is fun and engaging for our students! Regarding the support and partnership, they are always on top of everything. Small issues are resolved quickly, and that is not typical with other EdTech companies.
Donna Woods
CTE Cyber Pathway Instructor, Moreno Valley United School District